Monday, December 05, 2011
Penn State Password Management Upgrade
The Password Management page, work.psu.edu/password, will feature three options for users. The first option to change one's password remains unchanged, while a process to create/update security questions will be available along with a section for forgotten passwords.
In order to take full advantage of the upgrade, however, security questions must be set. By establishing security questions through the Password Management page, users will be able to reset their Access Account password if forgotten or expired. This function will be accessible from anywhere that there is an Internet connection.
If users opt out of enabling the security questions, they will need to follow the current procedures in place should their Access Account password expire, or is forgotten; as such, they must visit a signature station at one of the University's campuses, or contact the ITS Account Services Office at the University Park campus.
Ag IT STRONGLY RECOMMENDS that you setup Security Questions to be able to reset your Access Account password in the event that it has expired or has been forgotten.
See How To Update Your Penn State Access Account Security Questions.
Note: County Extension Staff Only - If you don't know your Penn State ID number, you may contact Extension Payroll at 814-865-5410. Staff can look up your 9 digit Penn State ID number. If there are several county-based staff who need to know their Penn State ID number, please create a list of Access Account UserIDs, First and Last Names for her. In addition, you do NOT need to provide a SSN number to get your Penn State ID number. SSN numbers should never be sent via email in any case.
Thursday, July 07, 2011
Update Released for Adobe Flash Player (version 10.3.181.34)
On June 30, 2011 Adobe released a update for Adobe Flash Player.
Note: This is NOT a security update.
Summary
Adobe Flash Player 10.3.181.34 addresses compatibility issues with some content using cross-domain policy files.
Action Required: None
If you want to update to the most current version, see our How To Install Updates to Adobe Flash Player, http://agsci.psu.edu/it/how-to/install-updates-to-adobe-flash-player.
Note: The above steps are written for Internet Explorer on a Windows computer. Your account on the computer must be an Administrator to follow these steps. If your account is not an Administrator and are using a College of Ag Enterprise Network computer, you can submit a Help Request to have the update applied for you.
Note: If you use multiple browsers, perform the check for each browser you have installed on your computer.
Wednesday, June 15, 2011
Security Update Released for Adobe Flash Player (version 10.3.181.26)
On June 14, 2011 Adobe released a Security advisory called Security update available for Adobe Flash Player that announced the availability of an update to their Flash Player 10 software.
Note: There are reports that this vulnerability is being exploited in the wild in targeted attacks via a malicious Web page. The advisory states in part:
Summary
A critical vulnerability has been identified in Adobe Flash Player 10.3.181.23 and earlier versions for Windows, Macintosh, Linux and Solaris, and Adobe Flash Player 10.3.185.23 and earlier versions for Android. This memory corruption vulnerability (CVE-2011-2110) could cause a crash and potentially allow an attacker to take control of the affected system. There are reports that this vulnerability is being exploited in the wild in targeted attacks via malicious Web pages.
Action Required: Ag IT recommends that you update the Adobe Flash Player on your Enterprise machine (or other devices that use Adobe Flash).
For steps, see our How To Install Updates to Adobe Flash Player, http://agsci.psu.edu/it/how-to/install-updates-to-adobe-flash-player.
Note: If you use multiple browsers, perform the check for each browser you have installed on your computer.
Security Update Available for Adobe Reader and Acrobat
Action Required: Ag IT recommends that College of Ag Science faculty and staff update any Adobe products to the current version.
Note: Along with applying this update, we also recommend that you follow these steps to Secure Adobe Reader to Prevent Malware once you have your Adobe products updated!!
- Open Adobe Reader or Adobe Acrobat Professional.
- From the Help menu choose Check for Updates.
- If updates were found, follow the on-screen steps to update.
Note: If an update is downloaded, close Adobe before applying the update.
Then re-open Adobe. Repeat steps 1 - 3 until no more updates are available.
Note: If the automatic updater does not find the latest updates, and your version is not the most current one, go to the Acrobat for Windows downloads page. Scroll down to locate the update for your version. Download and install.
Note: Earlier versions of Adobe Acrobat Professional (version 8 or lower) will not receive this patch. This updates represent an out-of-cycle release.
The Adobe Security bulletin, Security Updates available for Adobe Reader and Acrobat, has additional information and links.
Tuesday, June 07, 2011
Oracle Java Standard Edition (SE) 6 Update 26 Released
Action Required:
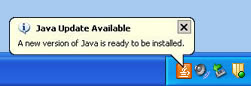
If you see the Java Update icon
Note: We recommend that you do not install any offered "extras" like Carbonite Backup, Microsoft's Bing Toolbar, MSN Toolbar, or OpenOffice.org Installer. Please un-check these options if they appear.
Or, our How To Update Sun's Java Software has complete steps on how to install Java from either the "Java Update Available" message or how to download and install Java manually .
Fixed:
Java SE 6 Update 26 contains 17 new security vulnerability fixes for Oracle Java SE. All these vulnerabilities may be remotely exploitable without authentication, i.e., may be exploited over a network without the need for a username and password.
Oracle Update Release Notes can be found here: http://www.oracle.com/technetwork/java/javase/releasenotes-136954.html
Note:
Java is a programming language and computing platform first released by Sun Microsystems in 1995. Java Standard Edition or Java SE is used by your computer to run certain web based applications. These may include web based training applications.
http://www.java.com/en/about/
Monday, June 06, 2011
Security Update Released for Adobe Flash Player (version 10.3.181.23)
On June 5, 2011 Adobe released a Security advisory called Security update available for Adobe Flash Player that announced the availability of an update to their Flash Player 10 software.
Note: There are reports that this vulnerability is being exploited in the wild in targeted attacks via a malicious Web page. The advisory states in part:
Summary
An important vulnerability has been identified in Adobe Flash Player 10.3.181.16 and earlier versions for Windows, Macintosh, Linux and Solaris, and Adobe Flash Player 10.3.185.22 and earlier versions for Android. This universal cross-site scripting vulnerability (CVE-2011-2107) could be used to take actions on a user's behalf on any website or webmail provider, if the user visits a malicious website. There are reports that this vulnerability is being exploited in the wild in active targeted attacks designed to trick the user into clicking on a malicious link delivered in an email message.
Action Required: Ag IT recommends that you update the Adobe Flash Player on your Enterprise machine (or other devices that use Adobe Flash).
For steps, see our How To Install Updates to Adobe Flash Player, http://agsci.psu.edu/it/how-to/install-updates-to-adobe-flash-player.
Note: If you use multiple browsers, perform the check for each browser you have installed on your computer.
Thursday, June 02, 2011
Adobe Flash Player Update Released for Internet Explorer
Summary
Flash Player 10.3.181.16 addresses an issue with hardware acceleration on some systems with Intel HD Graphics adapters when viewing SWF content in Internet Explorer 9. With Flash Player 10.3.181.14 installed, SWF content appeared in the upper-left corner of the screen.
Action Required: Ag IT recommends that you update the Adobe Flash Player on your Enterprise machine even though this update does not fix a security vulnerability. This update can be installed on computers using earlier versions of Internet Explorer as well.
For steps, see our How To Install Updates to Adobe Flash Player, http://agsci.psu.edu/it/how-to/install-updates-to-adobe-flash-player.
Note: Keeping 3rd party software up-to-date is GOES A LONG WAY to keep your computer safe from being infected by malware.
How To Download Latest Updates for Enterprise Dell Computers
Monday, May 16, 2011
Security Update Released for Adobe Flash Player (v10.3.181.14)
Note:
The advisory states in part: There are reports of malware attempting to exploit one of the vulnerabilities, CVE-2011-0627, in the wild via a Flash (.swf) file embedded in a Microsoft Word (.doc) or Microsoft Excel (.xls) file delivered as an email attachment targeting the Windows platform. However, to date, Adobe has not obtained a sample that successfully completes an attack.
Summary
Critical vulnerabilities have been identified in Adobe Flash Player 10.2.159.1 and earlier versions (Adobe Flash Player 10.2.154.28 and earlier for Chrome users) for Windows, Macintosh, Linux and Solaris, and Adobe Flash Player 10.2.157.51 and earlier versions for Android. These vulnerabilities could cause the application to crash and could potentially allow an attacker to take control of the affected system.
Action Required: Ag IT recommends that you update the Adobe Flash Player on your Enterprise machine (or other devices that use Adobe Flash) to mitigate the effects of malicious SWF (Flash) files that you might view in your web browser, Word, or Excel file.
For steps, see our How To Install Updates to Adobe Flash Player, http://agsci.psu.edu/it/how-to/install-updates-to-adobe-flash-player.
Note: If you use multiple browsers, perform the check for each browser you have installed on your computer.
Note: Additional help can be found at Adobe Support:
- Troubleshoot Flash Player installation | Windows
- Troubleshoot Flash Player | Mac OS
- Flash Player doesn't work | Windows 7
Tuesday, May 03, 2011
Oracle Java Standard Edition (SE) 6 Update 25 Released
Action Required:

If you see the Java Update icon
Note: We recommend that you do not install any offered "extras" like Carbonite Backup, Microsoft's Bing Toolbar, MSN Toolbar, or OpenOffice.org Installer. Please un-check these options if they appear.
Or, our How To Update Sun's Java Software has complete steps on how to install Java from either the "Java Update Available" message or how to download and install Java manually .
Fixed:
Java SE 6u25 does not add any fixes for security vulnerabilities beyond those in Java SE 6u24. Users who have Java SE 6u24 have the latest security fixes and do not need to upgrade to this release to be current on security fixes.
In Java SE 6 Update 25 support has been added for the Internet Explorer 9, Windows 7 with SP1, Firefox 4, and Chrome 10.
Note:
Java software allows you to run applications called “applets” that are written in the Java programming language. These applets allow you to play online games, chat with people around the world, calculate your mortgage interest, and view images in 3D. These may include web based training applications.
http://www.java.com/en/about/
Friday, April 22, 2011
Security Update Available for Adobe Reader and Acrobat
Action Required: Ag IT recommends that College of Ag Science faculty and staff update any Adobe products to the current version.
Note: Along with applying this update, we also recommend that you follow these steps to Secure Adobe Reader to Prevent Malware once you have your Adobe products updated!!
- Open Adobe Reader or Adobe Acrobat Professional.
- From the Help menu choose Check for Updates.
- If updates were found, follow the on-screen steps to update.
Note: If an update is downloaded, close Adobe before applying the update.
Then re-open Adobe. Repeat steps 1 - 3 until no more updates are available.
Note: If the automatic updater does not find the latest updates, and your version is not the most current one, go to the Acrobat for Windows downloads page. Scroll down to locate the update for your version. Download and install.
Note: Earlier versions of Adobe Acrobat Professional (version 8 or lower) will not receive this patch. This updates represent an out-of-cycle release.
The Adobe Security bulletin, Security Updates available for Adobe Reader and Acrobat, has additional information and links.
Saturday, April 16, 2011
Security Update Released for Adobe Flash Player
On April 15, 2011 Adobe released a Security advisory called Security update available for Adobe Flash Player that announced the availability of an update to their Flash Player 10 software.
Note: There are reports that this vulnerability is being exploited in the wild in targeted attacks via a malicious Web page, or a Flash (.swf) file embedded in a Microsoft Word (.doc) or Microsoft Excel (.xls) file delivered as an email attachment, targeting the Windows platform. The advisory states in part:
Summary
A critical vulnerability has been identified in Adobe Flash Player 10.2.153.1 and earlier versions (Adobe Flash Player 10.2.154.25 and earlier for Chrome users) for Windows, Macintosh, Linux, and Solaris, and Adobe Flash Player 10.2.156.12 and earlier versions for Android. This vulnerability (CVE-2011-0611), as referenced in Security Advisory APSA11-02, could cause a crash and potentially allow an attacker to take control of the affected system.
Action Required: Ag IT recommends that you update the Adobe Flash Player on your Enterprise machine (or other devices that use Adobe Flash) to mitigate the effects of malicious SWF (Flash) files that you might view in your web browser, Word, or Excel file.
For steps, see our How To Install Updates to Adobe Flash Player, http://agsci.psu.edu/it/how-to/install-updates-to-adobe-flash-player.
Note: If you use multiple browsers, perform the check for each browser you have installed on your computer.
Tuesday, March 22, 2011
Adobe Releases Multiple Security Updates, March 2011
Adobe addressed vulnerabilities in these products that that could cause the application to crash and allow an attacker to take control of the affected system.
Action Required: Ag IT recommends that College of Ag Science faculty and staff update any Adobe products to the current version.
Adobe Reader and Adobe Acrobat
- To update Adobe Reader 9 to the current version, follow our How To Install and Configure Adobe Reader v9 for Windows.
- If your computer has Adobe Acrobat Professional v9 or vX installed, you should be able to use the built-in Updater program to update the software.
a) From the Help menu choose Check for Updates.
b) If updates were found, follow the on-screen steps to update.
Note: If an update is downloaded, close Adobe before applying the update. Then re-open Adobe. Repeat steps a - b until no more updates are available.
Note: If the automatic updater does not find the latest updates, and your version is not the most current one, go to the Acrobat for Windows downloads page. Scroll down to locate the update for your version. Download and install.
Note: Along with applying this update, we also recommend that you follow these steps to Secure Adobe Reader to Prevent Malware once you have your Adobe products updated!!
Note: Earlier versions of Adobe Acrobat Professional (version 8 or lower) will not receive this patch. This updates represent an out-of-cycle release.
- To update Adobe Flash Player to the current version, follow our How To Install Updates to Adobe Flash Player, http://agsci.psu.edu/it/how-to/install-updates-to-adobe-flash-player.
Note: If you use multiple browsers, perform the check for each browser you have installed on your computer.
Thursday, March 03, 2011
Acrobat 9.4.2 Update Causes Printing Problems
- Error: "Before you can perform print-related tasks such as page setup or printing a document, you need to install a printer."
- Nothing happens when you click OK in the Print dialog box. For example, no progress bar appears and nothing is printed.
http://kb2.adobe.com/cps/891/cpsid_89178.html
Wednesday, February 16, 2011
Oracle Java Standard Edition (SE) 6 Update 24 Released
Action Required:

If you see the Java Update icon
Note: We recommend that you do not install any offered "extras" like Carbonite Backup, Microsoft's Bing Toolbar, MSN Toolbar, or OpenOffice.org Installer. Please un-check these options if they appear.
Or, our How To Update Sun's Java Software has complete steps on how to install Java from either the "Java Update Available" message or how to download and install Java manually .
Fixed:
Java SE 6 Update 24 contains a fix for a security vulnerability that allowed an attacker to cause "a complete denial of service" on your computer. If a Java application attempted tp convert "2.2250738585072012e-308" into a floating point number in Java, the bug caused an endless loop that resulted in a 100% load on your computer's processor.
Note:
Java is a programming language and computing platform first released by Sun Microsystems in 1995. Java Standard Edition or Java SE is used by your computer to run certain web based applications. These may include web based training applications.
http://www.java.com/en/about/
Wednesday, February 09, 2011
Adobe Releases Multiple Security Updates
Adobe addressed vulnerabilities in these products that that could cause the application to crash and allow an attacker to take control of the affected system.
Action Required: Ag IT recommends that College of Ag Science faculty and staff update any Adobe products to the current version.
Adobe Reader and Adobe Acrobat
- To update Adobe Reader 9 to the current version, follow our How To Install and Configure Adobe Reader v9 for Windows.
- If your computer has Adobe Acrobat Professional v9 or vX installed, you should be able to use the built-in Updater program to update the software.
a) From the Help menu choose Check for Updates.
b) If updates were found, follow the on-screen steps to update.
Note: If an update is downloaded, close Adobe before applying the update. Then re-open Adobe. Repeat steps a - b until no more updates are available.
Note: If the automatic updater does not find the latest updates, and your version is not the most current one, go to the Acrobat for Windows downloads page. Scroll down to locate the update for your version. Download and install.
Note: Along with applying this update, we also recommend that you follow these steps to Secure Adobe Reader to Prevent Malware once you have your Adobe products updated!!
Note: Earlier versions of Adobe Acrobat Professional (version 8 or lower) will not receive this patch. This updates represent an out-of-cycle release.
- To update Adobe Flash Player to the current version, follow our How To Install Updates to Adobe Flash Player, http://agsci.psu.edu/it/how-to/install-updates-to-adobe-flash-player.
Note: If you use multiple browsers, perform the check for each browser you have installed on your computer.
Monday, February 07, 2011
USB drive becomes 'PENDRIVE' - Remove AUTORUN.INF virus
Computers have become infected via the use of USB drives at conferences in particular. If your USB is placed into an infected machine, the drive name will be listed as PENDRIVE. If you place this drive into another Windows machine, the virus will be implanted there, ready to infect the next USB drive attached to the computer. This will continue to spread the virus via other USB drives to other computers.
NOTE: You should not insert an infected USB drive (e.g. memory stick) into any other computers until the virus is cleaned.
Malwarebytes' Anti-Malware can detect and remove most Malware with no further actions required for free. You should install it first to be sure you can scan and double check for the AUTORUN.INF virus.
Download Malwarebytes' Anti-Malware
- Go to this link, click the Download Latest Version. Save the file to your desktop.
http://www.filehippo.com/download_malwarebytes_anti_malware/ - Double-click on the mbam-setup.exe (where the x represent numbers) to install the application.
- When the installation begins, follow the prompts and do not make any changes to default settings.
- When installation has finished, make sure you leave the first choice checked but un-check the 2nd.
[check] Update Malwarebytes' Anti-Malware
[uncheck] Launch Malwarebytes' Anti-Malware - Click Finish. Wait for the program to update. Click OK.
Block the AUTORUN.INF virus
These steps will tell Windows to not execute the information in any AUTORUN.INF file that may be present. This is a great method to prevent Windows from being infected by virus through autorun.inf method. The only downside of this is that if you insert a USB Drive, CD or DVD with software on it, you have to open it by manually.
- Click Start, choose All Programs, and open Notepad.
- Copy the text below and paste it into the blank Notepad window.
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping\Autorun.inf]
@="@SYS:DoesNotExist" - Save the file with this name to the desktop (be sure the extension is .reg and not .txt):
NoAutoRun.REG - Close Notepad.
- Double click on NoAutoRun.REG and click Yes if you're asked "Are you sure you want to add the information in C:\NoAutoRun.reg to the registry?"
- Insert the USB drive.
- Open My Computer. Make a note of the Drive Letter assigned to the USB drive (for example Drive letter E).
- Click Start, choose Run.
- Type cmd into the Open box. Press Enter.
Note: This will open a command prompt window. Within the command prompt window type the following text in bold and then press Enter. - Type cd\ and press Enter.
Note: In step 5, you will type the drive letter - Type the drive letter followed by a colon (for example E: or F:). Press Enter.
Note: In step 7 there is no space between the dashes and the letters but there is a space after the letters. - Type attrib -r -h -s autorun.inf and press Enter.
- Type del autorun.inf and press Enter.
Note: If you see a "file not found" message, double check the spelling for Step 8. You may repeat. But the file may not be present on the drive (so it is not infected). - If you have a second USB drive, insert and repeat steps 1 through 8.
- Final Step: Open Malwarebytes, choose to do a Full Scan. Scan both the C drive and the USB drive (s). If anything is found, click Show Results. Remove any infections.